Healthcare organizations are increasingly relying on HIPAA compliant technology to protect patient data. Healthcare providers are now embracing solutions like HIPAA-compliant texting, compliant hosting, and HIPAA compliant apps to safeguard protected health information. New technologies continue to enhance security, ensuring that health information and electronic protected health information remain secure under strict HIPAA guidelines and regulations.
At Aloa, we deliver high-quality software projects that meet HIPAA compliance. With our project management framework, we leverage top industry trends through our network of vetted partners. We guide healthcare organizations, ensuring they meet the latest HIPAA guidelines and technical safeguards, like secure cloud storage providers and managed AWS provider services. We provide continuous support for hosting services, patient data security, and business associates agreements.
Building on proven strategies, this guide explores key aspects of HIPAA compliant technology. We cover the impact of new technologies on HIPAA compliance, focusing on cloud solutions, HIPAA-compliant apps, and secure texting for healthcare providers. You’ll also learn about HIPAA-compliant hosting, including dedicated servers and private cloud setups. By the end, you’ll understand how these technologies safeguard patient data and meet HIPAA regulations.
Let's dive in!
What Is HIPAA Compliant Technology?
HIPAA compliant technology refers to secure solutions designed to meet the HIPAA requirements for protecting sensitive health information. It ensures healthcare providers and their partners comply with the Health Insurance Portability and Accountability Act (HIPAA). Businesses must follow the HIPAA security rule to avoid unauthorized access and data breaches.
Key Features of HIPAA Compliant Technology
HIPAA compliant technology includes several essential features to protect sensitive information and ensure compliance with HIPAA security rules. Let’s explore five key features:
- Data Encryption: Encrypting data in transit and at rest protects against unauthorized access. HIPAA requires data encryption to safeguard patient information on storage servers and during transmission, which is critical for maintaining security on cloud hosting platforms like Microsoft Azure and Amazon Web Services.
- Offsite Backups and Disaster Recovery: HIPAA compliant technology must include robust offsite backups and disaster recovery strategies. These ensure that data remains accessible even after hardware failures or security incidents. HIPAA Vault and Liquid Web solutions specialize in creating secure backup environments for covered entities.
- Access Controls and Physical Safeguards: Strong access controls prevent unauthorized personnel from accessing sensitive information. Physical safeguards, such as server cabinets and strict physical security policies within data centers, ensure that only authorized users can access protected health data. Hosting solutions such as HIPAA hosting focus on implementing these measures.
- Business Associate Agreement (BAA): Any hosting provider or cloud service provider must sign a business associate agreement to comply with HIPAA privacy rules. This agreement ensures the provider follows all necessary security measures for data protection and accountability in line with HIPAA requirements.
- Database Management and Physical Security Policies: Effective database management requires strict physical security policies within data centers. These security measures, such as server cabinets and locked storage servers, ensure compliance with HIPAA security rules—providers like HIPAA Vault and Liquid Web offer compliant hosting solutions that adhere to these physical safeguards.
HIPAA compliant technology remains vital for protecting patient data through security measures like data encryption, offsite backups, and access controls. Microsoft Azure, Amazon Web Services, and Liquid Web provide compliant hosting solutions that prioritize security and prevent unauthorized access to healthcare data.
HIPAA Compliant Hosting
HIPAA compliant hosting is a secure hosting solution that meets the strict regulations outlined in the Health Insurance Portability and Accountability Act (HIPAA). This hosting safeguards protected health information (PHI) with various security measures, including encryption, access controls, and regular audits. Healthcare organizations rely on HIPAA compliant technology like this to ensure patient data remains private and secure, reducing the risk of unauthorized access or breaches.
Emerging Threats in HIPAA Compliant Hosting
New technologies and evolving cyber threats constantly challenge the security of HIPAA compliant hosting. Understanding these risks allows healthcare organizations to protect their data proactively.

- Cloud Infrastructure Vulnerabilities: Cloud infrastructure provides flexibility but also introduces risks. Misconfigurations in cloud setups can expose PHI to unauthorized users. Many organizations overlook security gaps in cloud storage, which can result in data leaks.
- Hybrid Environments: A hybrid environment, which combines on-premises and cloud hosting, presents additional challenges for HIPAA compliance. Moving data between environments creates opportunities for data breaches if not done securely.
- Ransomware Attacks: Ransomware continues to grow as a threat to healthcare systems. Attackers can infiltrate hosting environments, encrypt sensitive data, and demand payment to restore access. Implementing strong security protocols and regular data backups is critical to mitigating this threat.
- Third-Party Risks: Organizations using third-party service providers for hosting must ensure compliance across all parties. Failure to vet third-party services can result in non-compliance, even if the primary hosting provider adheres to HIPAA regulations.
How to Implement HIPAA Compliant Hosting
Implementing HIPAA compliant hosting requires careful planning and execution. Here are key steps to ensure compliance and protect patient data.
- Choose a HIPAA-Compliant Hosting Provider: Select a hosting provider that meets all HIPAA requirements. Providers should offer encryption, regular security audits, and strict access control measures. They should also sign a Business Associate Agreement (BAA) confirming their responsibility for protecting PHI.
- Encrypt All Data: Data encryption ensures that PHI remains unreadable to unauthorized users. Encryption should be used for data at rest and in transit to comply with HIPAA's security rules.
- Implement Access Controls: Strict access controls limit who can view or modify PHI. Use multi-factor authentication and role-based access controls to ensure that only authorized personnel can access sensitive data.
- Regular Audits and Monitoring: Conduct regular security audits and continuous monitoring of your hosting environment to identify potential vulnerabilities before they lead to breaches. Automated monitoring systems can detect unusual activity and flag potential security issues.
HIPAA compliant technology plays a critical role in protecting healthcare data. Choosing the right hosting solution ensures compliance and reduces the risk of data breaches. Organizations must stay vigilant against emerging threats, implementing strong encryption, access controls, and security protocols to keep patient information safe.
HIPAA Compliant Texting
HIPAA-compliant texting allows healthcare professionals to send and receive patient information through text messages without compromising privacy. This method meets the standards set forth in the Health Insurance Portability and Accountability Act (HIPAA) and ensures that all Protected Health Information (PHI) remains confidential and secure during transmission. Choosing a HIPAA-compliant SMS service is a practical way to support secure, compliant texting for patient communication.
HIPAA compliant hosting offers practical applications such as secure file sharing, encrypted communication, and data storage solutions for healthcare providers. It plays a crucial role in protecting patient privacy and meeting regulatory requirements.
HIPAA Rules and Regulations for SMS Text Messaging
Understanding HIPAA rules for SMS text messaging is essential for maintaining compliance. These regulations govern how PHI should be handled when texting or using CRM messaging platforms as communication tools
- Secure Encryption: All text messages containing PHI must use end-to-end encryption to ensure that only authorized parties can access the information, keeping it safe from interception.
- Access Controls: Implement strict access controls to ensure only authorized personnel can send or receive PHI via text messages. This involves user authentication measures like strong passwords and two-factor authentication.
- Audit Controls: Maintain audit trails that record all access to PHI to track who accessed what information and when, which is vital for detecting unauthorized access.
- Automatic Logoff: Devices used for texting PHI should have automatic logoff features to reduce the risk of unauthorized access if a device is left unattended.
- Breach Notification Procedures: Establish protocols for notifying affected individuals and authorities during a security breach. Prompt notification is a requirement under HIPAA regulations.
Following these HIPAA regulations for SMS text messaging ensures that healthcare organizations remain compliant while protecting sensitive patient data. A proactive approach to these rules helps minimize risks.
Best Practices for Sending Safe and Secure HIPAA SMS and Text Messages
Adopting best practices enhances the security of HIPAA compliant texting. These measures help maintain compliance and protect patient information.

- Use HIPAA Compliant Messaging Apps: Select applications designed to meet HIPAA requirements. These apps include features like encryption and secure login.
- Implement Strong Password Policies: Require complex passwords and regular password changes. Strong passwords protect against unauthorized access to messaging apps.
- Regular Employee Training: Educate staff on HIPAA regulations and the importance of secure texting. Ongoing training keeps everyone informed about the latest compliance practices.
- Enable Remote Wipe Features: Ensure that devices can be remotely wiped if lost or stolen. This prevents PHI from falling into the wrong hands.
- Conduct Routine Security Assessments: Regularly evaluate the security measures in place. Assessments help identify vulnerabilities in your HIPAA compliant technology and allow for timely improvements.
Following best practices for HIPAA compliant texting significantly reduces the risk of data breaches and ensures ongoing compliance. These simple steps safeguard patient data and ensure secure communication in healthcare organizations.
What Are HIPAA Compliant Apps?
HIPAA compliant apps are mobile or web applications designed to protect sensitive health information. They ensure patient data remains secure through encryption, access controls, and communication protocols. HIPAA compliant technology, including apps, must adhere to standards that prevent unauthorized access, ensuring healthcare providers stay compliant and avoid costly penalties.
Development Process for HIPAA Compliant Apps
Developing HIPAA compliant apps requires careful planning and execution. Here are five essential steps:
- Identify Compliance Requirements: Developers must understand HIPAA regulations before beginning the project. Knowing what is required helps align the app’s features with HIPAA compliant technology standards.
- Perform Data Encryption: Protecting patient data during transmission and storage is crucial. Encryption ensures that data remains secure, even if intercepted.
- Implement Access Control: Only authorized users should have access to sensitive health information. Strong access control measures restrict who can view or modify patient data.
- Conduct Regular Audits: HIPAA compliant apps must undergo regular audits to ensure they continue meeting security standards. These audits help identify system vulnerabilities and confirm that the app follows HIPAA compliant technology guidelines.
- Establish Emergency Data Backup: A secure backup system ensures that patient data remains accessible during emergencies and protects it from data loss.
Building HIPAA compliant apps involves following strict security measures at every stage. Developers must ensure their apps meet all HIPAA requirements, from encryption to access control. Integrating HIPAA compliant technology into the development process helps safeguard patient data while keeping healthcare providers compliant.
New Technologies and Their Impact on HIPAA Compliance
Recent advancements in technology have significantly impacted HIPAA compliant technology. Innovations such as artificial intelligence (AI) and blockchain enhance data security and operational efficiency. These technologies strengthen HIPAA compliance efforts, ensuring patient data remains protected across various platforms.
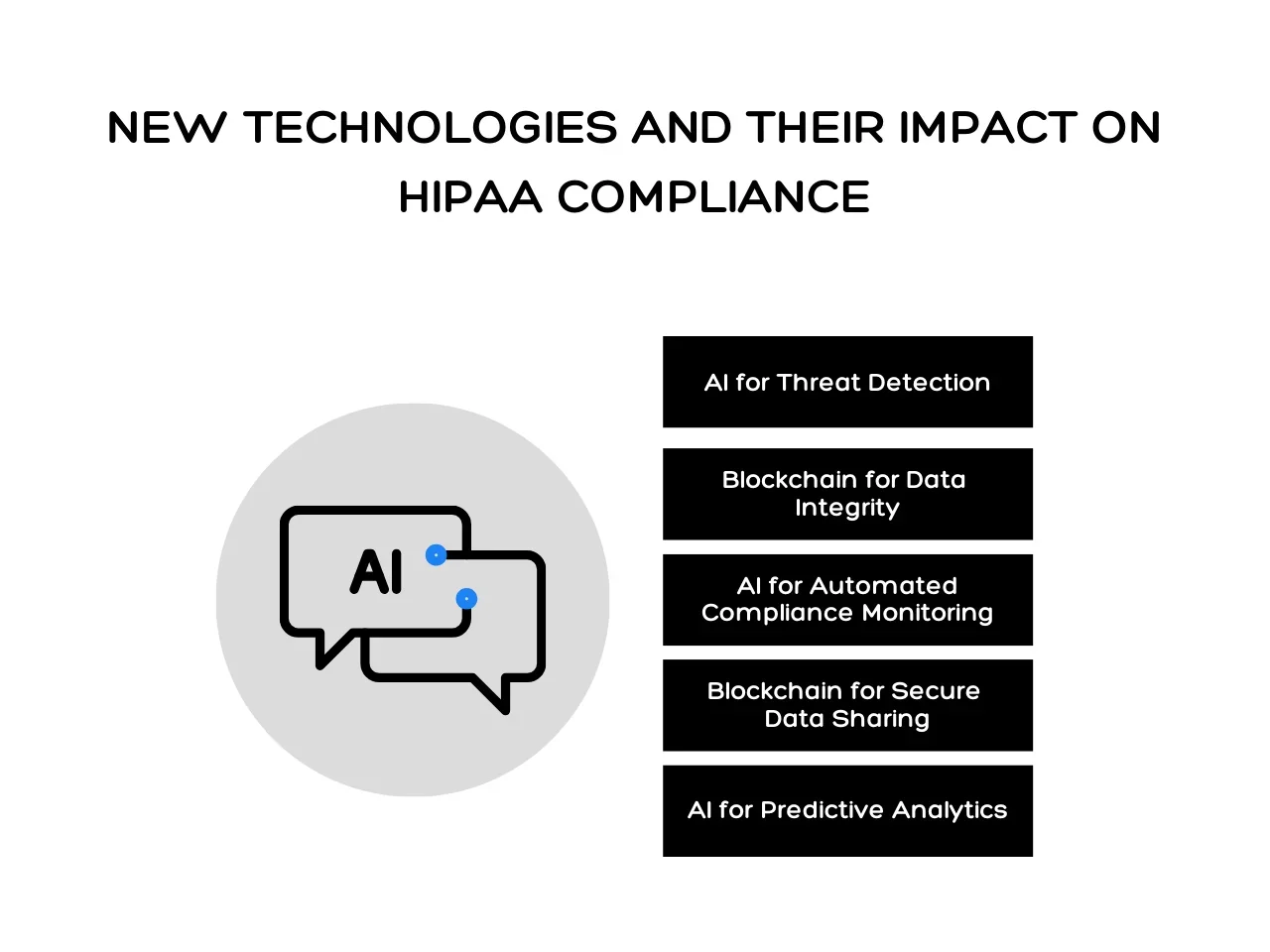
Here are five ways AI and blockchain improve HIPAA compliance:
- AI for Threat Detection: AI systems can monitor and detect potential security breaches in real-time, identifying unusual patterns and reducing the risk of unauthorized access. This enhances the security of HIPAA compliant technology.
- Blockchain for Data Integrity: Blockchain technology ensures data integrity. Once entered, data cannot be altered or deleted, providing transparency and maintaining compliance with HIPAA standards. It strengthens HIPAA compliant hosting and ensures secure record-keeping.
- AI for Automated Compliance Monitoring: AI tools streamline compliance by continuously monitoring systems to ensure they meet HIPAA compliant technology requirements. This reduces the workload for healthcare providers and IT teams.
- Blockchain for Secure Data Sharing: Blockchain enables secure, decentralized sharing of sensitive data between healthcare providers while maintaining compliance with HIPAA compliant texting and web hosting standards.
- AI for Predictive Analytics: AI helps predict potential security threats, allowing organizations to take preventive measures. This proactive approach secures HIPAA compliant apps and technology.
Leveraging AI and blockchain enhances HIPAA compliant technology, ensuring healthcare providers protect patient data while streamlining operations. These technologies offer practical solutions for maintaining compliance and meeting the evolving demands of the healthcare industry.
Key Takeaway
HIPAA compliant technology is crucial for protecting sensitive patient information. HIPAA compliant texting, hosting, and apps help healthcare providers meet legal requirements and safeguard data from unauthorized access. A secure HIPAA compliant software solution ensures that patient communication, records, and operations remain private and protected.
When developing healthcare software, businesses must carefully consider all aspects of compliance. Working with a HIPAA compliant development expert ensures that every detail, from secure messaging to encrypted hosting, meets the necessary standards. Telemedicine software, in particular, requires advanced security measures to handle patient data securely and efficiently.
Are you ready to enhance your security with HIPAA compliant technology? At Aloa, we guide healthcare providers in building secure, compliant solutions tailored to their needs. Our experts will ensure that your HIPAA-compliant software and systems exceed industry standards, safeguarding patient data every step of the way.

