Developing HIPAA-compliant software is paramount within the health tech industry to safeguard patient information. Adhering to the regulations of the Health Insurance Portability and Accountability Act (HIPAA), these solutions play a pivotal role in securing electronic health records (EHR).
By meticulously following HIPAA guidelines, the software not only ensures the safety of sensitive health data but also instills confidence among medical providers and patients alike.
Aloa, a software outsourcing company, ensures strict adherence to HIPAA regulations in every healthcare solution, prioritizing the security and privacy of patient information. In the past, Aloa has worked with PepCare to develop a custom-built healthcare platform for orthodontists consolidates all doctor-customer interactions into an easy to use dashboard.
This blog will guide you through the critical steps in creating software solutions that comply with HIPAA standards. By the end of this blog, you'll have a comprehensive understanding of how to prioritize HIPAA compliance, ensuring the development of secure and reliable healthcare software tailored for the healthcare industry.
Let's dive in!
What is HIPAA Compliant Software?
HIPAA compliant software refers to applications and systems designed to meet the HIPAA guidelines. These regulations are in place to safeguard the confidentiality, integrity, and availability of sensitive data information.
Such software, equipped with robust security measures like encryption, access controls, and audit trails, ensures that small businesses, healthcare organizations, and startups can handle electronically protected health information (ePHI) securely and in a privacy-centric manner.
HIPAA compliance software prevents unauthorized access to patient data, and fosters trust among healthcare providers and patients. Exploring a HIPAA compliance solution is integral in enhancing this trust and security, ensuring comprehensive protection of sensitive health information. Implementing these standards is crucial for avoiding legal repercussions and ensuring ethical practices within the health industry.
How to Develop HIPAA Compliant Software in 2024
Developing HIPAA compliant software in 2024 demands the integration of customer insights with effective software development, ensuring a harmonious blend of user needs and industry standards. Here are the crucial development processes essential for safeguarding healthcare data security throughout the software creation journey.
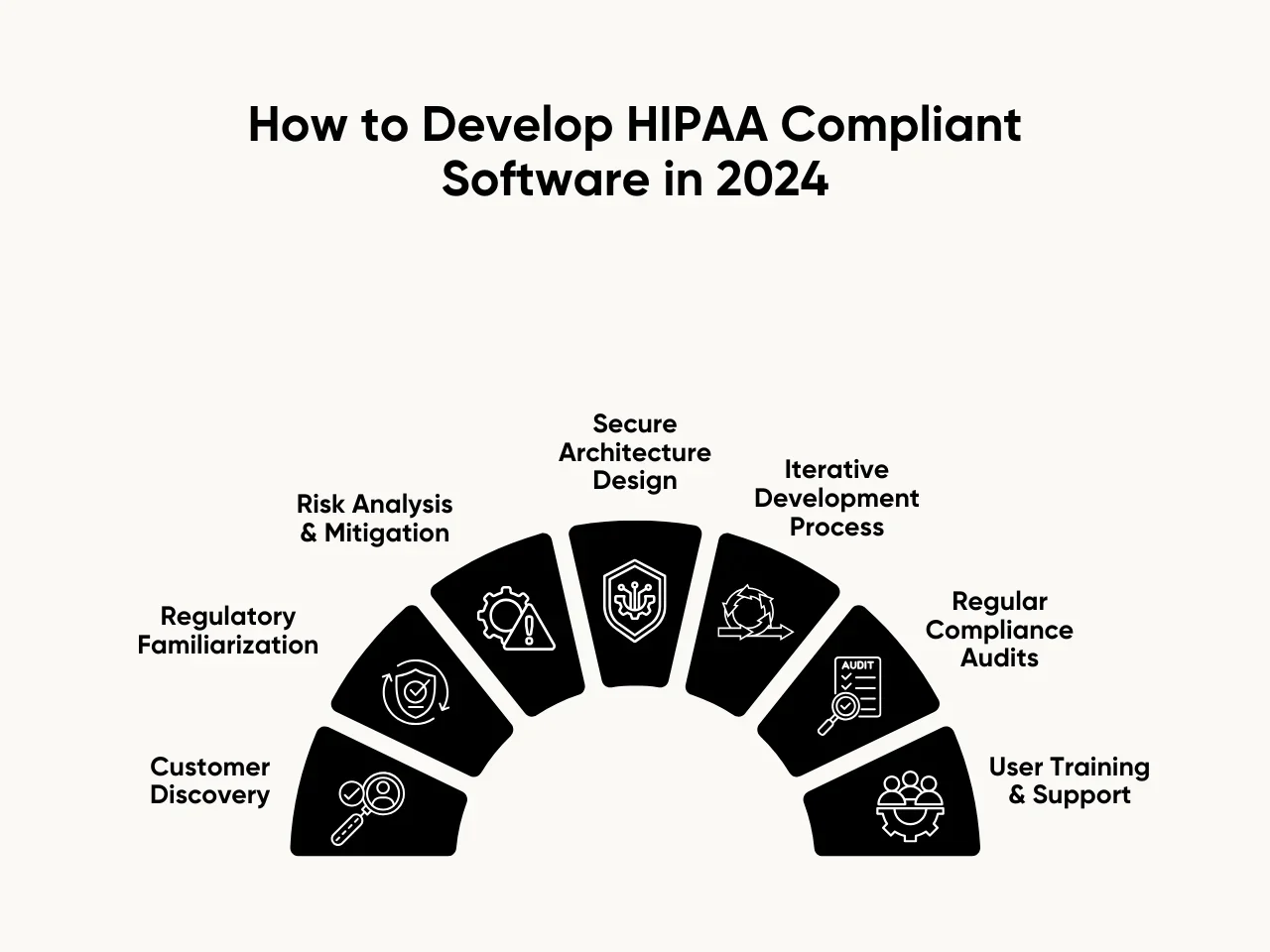
Step 1: Customer Discovery
Customer discovery is a critical phase in developing HIPAA compliant software where health tech developers engage in in-depth interviews with various stakeholders within the healthcare industry. These stakeholders may include healthcare providers, administrators, and other personnel managing patient data.
The purpose of these interviews is to gain a profound understanding of healthcare entities' specific needs and challenges in handling electronic health information. During these interviews, developers seek to uncover the intricacies of workflows, data management, and security concerns unique to each stakeholder.
By actively listening and engaging with stakeholders, developers aim to identify opportunities for improvement and innovation in creating software solutions that meet regulatory requirements and streamline and enhance the healthcare data management experience.
Step 2: Regulatory Familiarization
Regulatory familiarization is a critical foundation in developing HIPAA compliant software in 2024. To navigate the complex healthcare regulatory landscape successfully, developers must stay informed about the latest HIPAA regulations and guidelines.
Here are the key points to consider:
- Continuous Monitoring of Regulatory Updates: Stay informed about regulation changes from entities such as the Department of Health and Human Services (HHS) to align development processes with the latest standards.
- In-Depth Understanding of HIPAA Rules: Familiarize yourself with the specific requirements outlined in the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule to ensure comprehensive compliance.
- Legal Expert Consultation: Consider seeking advice from legal experts specializing in healthcare compliance to gain a nuanced understanding of regulatory nuances and potential legal implications.
- Integration into Software Development Life Cycle: Document and seamlessly integrate regulatory requirements into the software development life cycle to address compliance issues proactively at every stage.
By adhering to these critical points, developers can navigate the intricate regulatory landscape, ensuring their software aligns with the latest HIPAA standards and legal obligations in the evolving healthcare industry.
Step 3: Risk Analysis and Mitigation
Risk analysis and mitigation are crucial in creating HIPAA compliant software where developers carefully examine possible security issues. This involves looking at potential threats and vulnerabilities that could compromise the confidentiality and integrity of sensitive patient data.
The goal is to be like a detective, figuring out where the software might face challenges in keeping healthcare data safe. To do this, developers identify possible risks such as unauthorized access, data breaches, or system failures, including monitoring and addressing login attempts, and then establish security policies and data protection strategies to mitigate or minimize these dangers.
This can involve using strong encryption to protect information, securing access controls, and having backup plans if something goes wrong. By taking these preventive measures, developers aim to ensure that the software meets HIPAA standards and provides a robust defense against potential security threats.
Step 4: Secure Architecture Design
Secure architecture design is pivotal in developing HIPAA compliant software in 2024, ensuring robust protection for electronic protected health information (ePHI).
Here are the key points to consider:
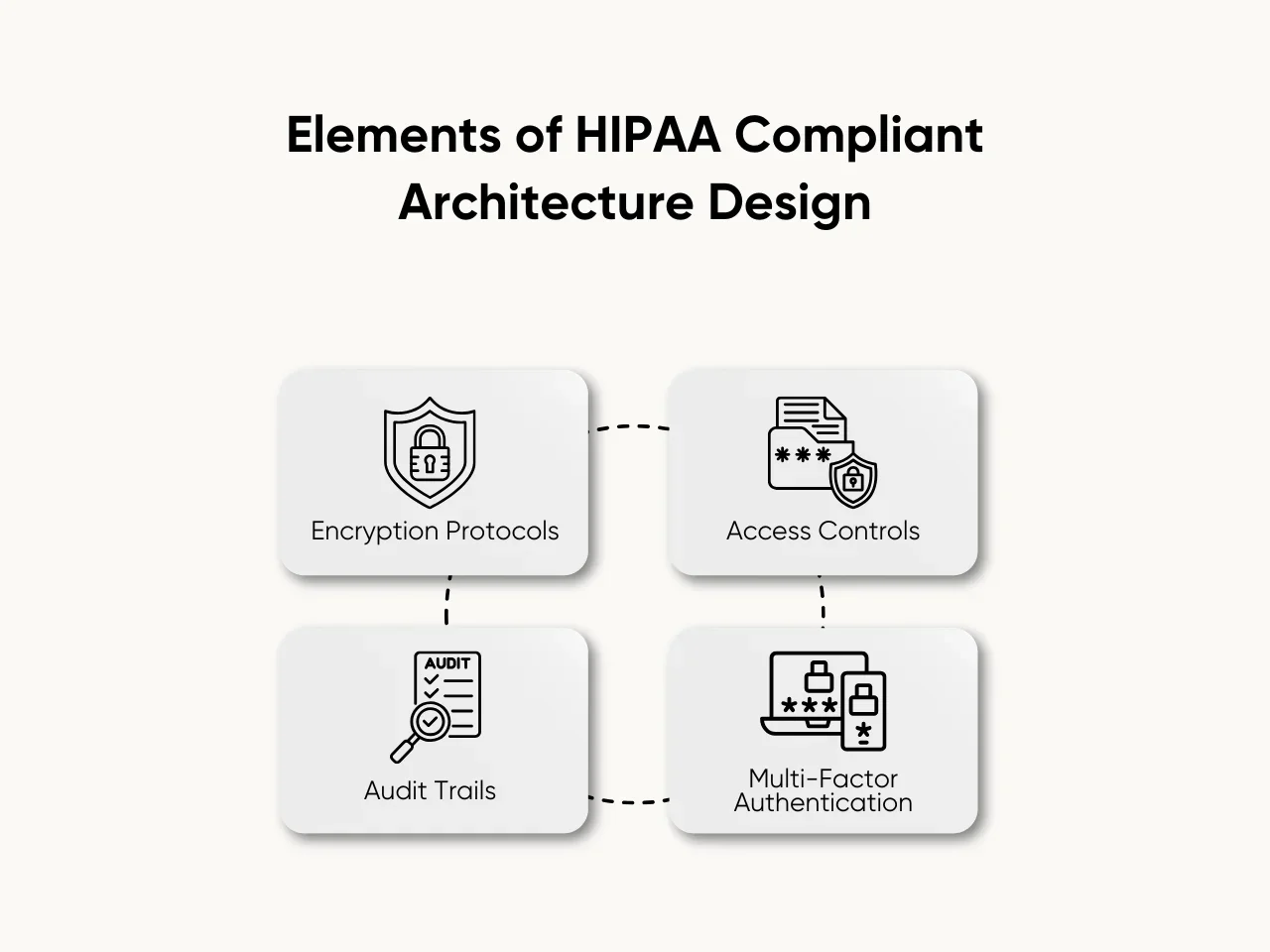
- Encryption Protocols: Employ robust encryption algorithms to secure data during transmission and storage, mitigating the risk of unauthorized access to sensitive health information.
- Access Controls: Implement stringent access controls to restrict system entry and limit user permissions, safeguarding ePHI against unauthorized or inappropriate access.
- Audit Trails: Integrate comprehensive audit trails that log and monitor user activities, enabling the tracking of data access and modifications for accountability and compliance purposes.
- Multi-Factor Authentication (MFA): Enhance security by incorporating multi-factor authentication, requiring users to provide multiple verification forms, such as passwords and biometrics, to access the software.
Incorporating these elements into the software's architecture fortifies its security posture, aligning it with HIPAA standards and promoting the safe handling of health information in the digital realm. Through these measures, developers will contribute significantly to their healthcare software's overall compliance and integrity.
Step 5: Iterative Development Process
The iterative development process is like building a puzzle where you start with a few pieces and add more, adjusting as you go. Instead of creating the entire software simultaneously, developers take a step-by-step approach, creating small parts and continually improving them.
This process involves creating a basic version of the software, often called a prototype, and sharing it with those who will use it, such as healthcare professionals. These users provide feedback on what works well and what needs improvement. Developers then make changes, like fine-tuning a melody, and present the updated version again for further feedback.
This cycle repeats until the software meets the desired standards, effectively addresses the evolving needs of the stakeholders, and ensures that the software remains flexible, adapting to any changes or new requirements that emerge during development. This constant loop of feedback and adjustments results in a finely tuned and highly functional software solution.
Step 6: Regular Compliance Audits
Regular compliance audits are crucial to developing HIPAA compliant software in 2024, providing a systematic approach to verifying and maintaining adherence to the ever-evolving regulatory landscape.
Here are the key points to consider:
- Scheduled Audits: Conduct regularly scheduled audits to systematically assess the software's compliance status and promptly identify and address potential gaps.
- Documentation Review: Thoroughly review and update documentation, including policies and procedures, to ensure they accurately reflect the current state of compliance with HIPAA standards.
- Risk Assessment: Perform regular risk assessments to identify and mitigate potential security vulnerabilities, adapting the software's features and configurations accordingly.
- Employee Training Evaluation: Assess the effectiveness of ongoing employee training programs to ensure staff members are consistently well-informed about the latest HIPAA requirements.
By incorporating these key points into the development process, developers can establish a continuous compliance program, promoting their HIPAA compliant software's long-term viability and effectiveness. Regular audits serve as proactive measures to uphold the integrity and security of healthcare data in the dynamic landscape of 2024.
Step 7: User Training and Support
User training and support, including cybersecurity, is crucial in maintaining the integrity of your HIPAA compliant software. Begin by developing a comprehensive training program for end-users, emphasizing the importance of adhering to HIPAA regulations during software utilization.
The training should cover critical aspects such as data security protocols, access controls, and properly handling protected health information (PHI). Ensure that users understand the potential risks associated with non-compliance and the significance of their role in maintaining a secure environment.
Additionally, establish a user-friendly help desk or support system to promptly address any queries, concerns, or issues that may arise during software operation. By prioritizing user education and providing continuous support, you contribute significantly to your software's overall compliance and security in the ever-evolving landscape of healthcare data management.
HIPAA Compliant Software Checklist Requirements
Ensuring the development and maintenance of HIPAA compliant software is paramount in the healthcare industry to safeguard sensitive patient information. To guide developers and healthcare organizations, here are the HIPAA compliant software checklist requirements to foster a robust and compliant software environment.
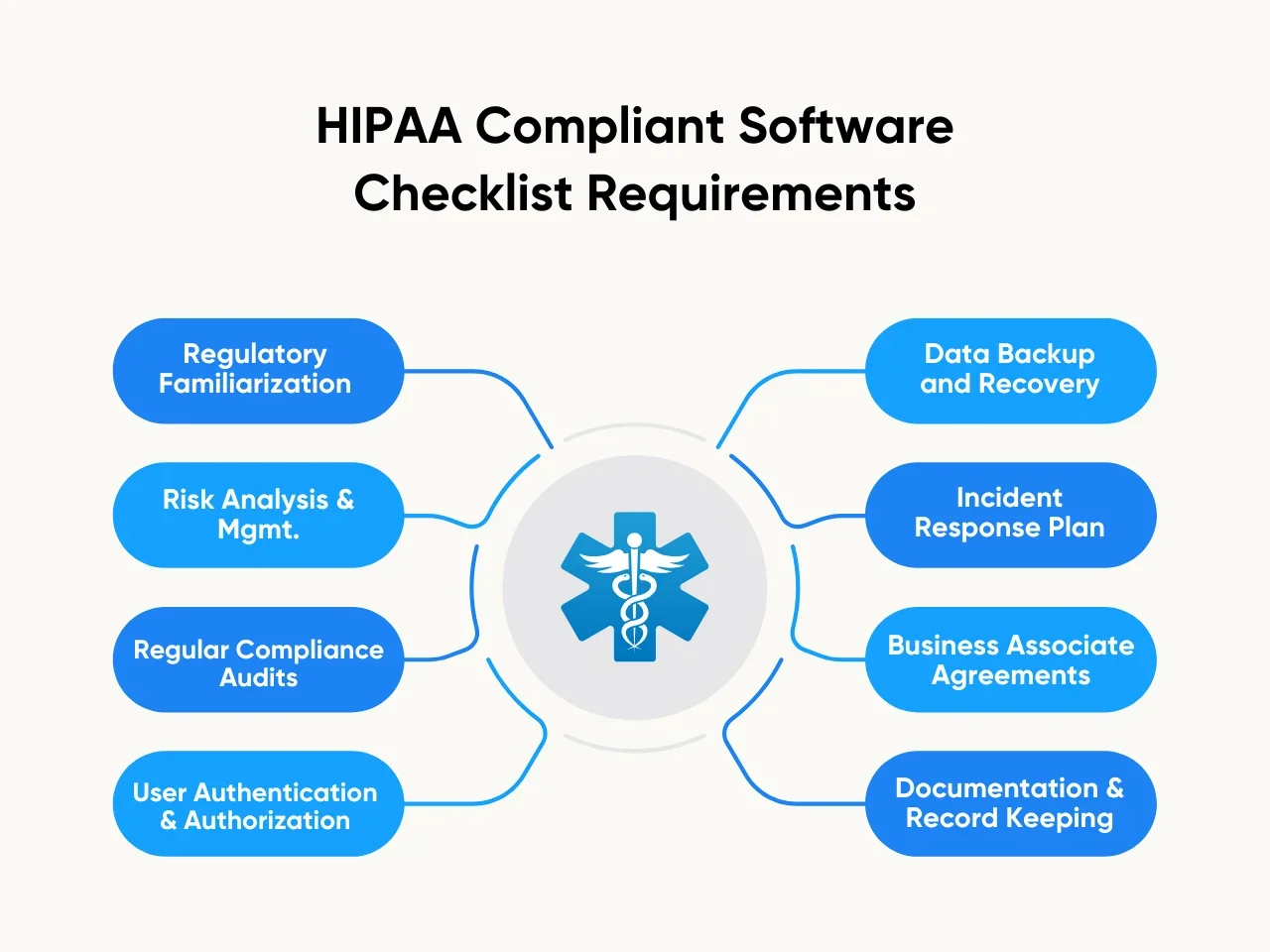
Regulatory Familiarization
- Stay updated on the latest HIPAA regulations and guidelines from the Department of Health and Human Services (HHS).
- Familiarize yourself with the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule.
Risk Analysis and Management
- Perform regular risk assessments to identify and mitigate potential security vulnerabilities.
- Establish protocols for ongoing risk management to address evolving threats and challenges.
Regular Compliance Audits
- Conduct scheduled audits to assess ongoing compliance with HIPAA standards.
- Review and update documentation, including policies and procedures, to reflect the latest compliance requirements.
- Perform risk assessments to identify and address potential security vulnerabilities.
User Authentication and Authorization
- Implement multi-factor authentication (MFA) for enhanced user authentication.
- Establish role-based access controls to ensure users only have access to the information necessary for their roles.
Data Backup and Recovery
- Establish robust data backup procedures to prevent data loss.
- Develop a comprehensive data recovery plan to quickly restore functionality during a data breach or system failure.
Incident Response Plan
- Develop and maintain an incident response plan to address potential security incidents promptly.
- Establish a clear communication plan to notify relevant parties during a data breach.
Business Associate Agreements (BAAs)
- Establish and maintain Business Associate Agreements with third-party vendors or service providers handling ePHI.
- Ensure that BAAs clearly outline the responsibilities and obligations regarding HIPAA compliance.
Documentation and Record Keeping
- Maintain detailed documentation of all security measures and compliance efforts.
- Keep records of audits, risk assessments, and training programs for future reference and regulatory purposes.
This comprehensive checklist allows developers and healthcare organizations to establish a robust framework for HIPAA compliant software development and ongoing maintenance. Regular adherence to these requirements is essential for safeguarding sensitive health information and ensuring compliance with HIPAA standards.
Essential Features of a HIPAA Compliant Software Solution
Securing patient data and ensuring regulatory compliance are pivotal in software development, whether for healthcare android app developers or other professionals in the field. Here are the key features of a HIPAA compliant software solution.

Admin Side Features of a HIPAA Compliant Software
- User Access Controls: Implement robust access controls to ensure that only authorized administrators can view or modify sensitive patient information, adhering to the principle of least privilege.
- Audit Trails and Logging: Maintain detailed audit trails and logs to track all activities within the software, enabling administrators to monitor user actions and facilitating swift response to any potential security incidents.
- Role-Based Permissions: Employ role-based permissions to tailor access levels based on job responsibilities, limiting access to specific functionalities and patient data by the user's role.
- Data Encryption: Utilize robust encryption methods for data at rest and in transit, ensuring that any stored or transmitted patient information remains secure from unauthorized access.
- Incident Response Tools: Integrate tools for incident response and breach notification, empowering administrators to promptly and efficiently address security incidents and comply with reporting requirements outlined in HIPAA.
User Side Features of a HIPAA Compliant Software
- Secure Login with Multi-Factor Authentication (MFA): Provide secure user logins with multi-factor authentication, enhancing identity verification and safeguarding against unauthorized access to patient information.
- Patient Data Confidentiality: Ensure that users can only access the patient data necessary for their roles, maintaining strict confidentiality and privacy by HIPAA regulations.
- Secure Messaging and Communication: Implement encrypted messaging features to facilitate secure communication among healthcare professionals while protecting the confidentiality of patient-related discussions.
- Consent Management: Include features for managing patient consent, allowing users to track and document patient authorization to use and disclose their protected health information (PHI).
- Access to Updated Privacy Policies: Provide easy access to updated privacy policies and training materials within the software interface, informing users about HIPAA compliance requirements and best practices.
Key Takeaway
In healthcare, constructing HIPAA compliant software is a cornerstone for ensuring the security and confidentiality of patient medical records. This process requires a continuous commitment to staying updated on the latest regulatory frameworks, prioritizing robust security features, and fostering a culture of compliance within the development team.
By embracing HealthTech trends and incorporating HIPAA-compliant practices, developers play a vital role in advancing secure healthcare applications, enhancing patient experiences, and upholding industry integrity in the digital era.
Elevate your HealthTech solutions with Aloa's proven expertise, exemplified in our successful development of HIPAA compliant software for Pepcare. Our experience with Pepcare uniquely positions us to navigate the intricacies of the healthcare industry.
Whether you're a small private practice clinic or part of a large-scale operation, trust Aloa to tailor solutions prioritizing security, compliance, and seamless functionality. Contact us at resources@aloa.co and let Aloa's be your assurance of gaining innovative and secure digital healthcare solutions.

